Aggressive penetration of workstream collaboration platforms in the enterprise has shifted over 50% of team communications to these collaboration platforms. Yet nearly 33% of all organizations still lack the capability to prevent or deter an insider incident or attack related to workstream collaboration applications. As insider accidents and inadvertent data breaches increasingly become the norm, investing in strong collaboration security has never been more vital. Mitigating risk in the workstream collaboration space covers a large surface area because it goes beyond traditional file and email data loss prevention (DLP) to include newer data types like chat streams, comments, meeting transcripts, etc.
Addressing collaboration security isn’t just another information security checkbox: apply too lax of a policy, and your business data will be at risk, but if too strict of policy is used, your business data will be driven into shadow IT solutions. The end goal of collaboration security is the art of achieving the right balance of usability and security, a balance that varies from company to company.
Why Collaboration Security is Unique
Preparing a framework and strategy is just the beginning. Collaboration and communication platforms pose constant risks that need to be monitored, measured, and managed efficiently. While it’s possible to apply a manual solution to this problem (e.g., address exposures through human intervention), such an approach is not sustainable or scalable. Approaching collaboration security effectively and efficiently requires intelligent software not only to manage problems as they occur but also to mitigate risk before an incident ever happens.
THE THREE M’S OF COLLABORATION SECURITY
The traditional model of controlling user and application policies, as well as permissions, have been found to be too cumbersome or over-reaching in the modern digital workplace. The normal IT top-down governance approach can sometimes cause users to shift to some level of shadow IT solution as a workaround.
One new InfoSec approach being advocated encourages enterprises to be much more forgiving regarding how they allow user behavior to initially dictate policy, and to then subsequently manage and remediate collaboration issues after the fact.
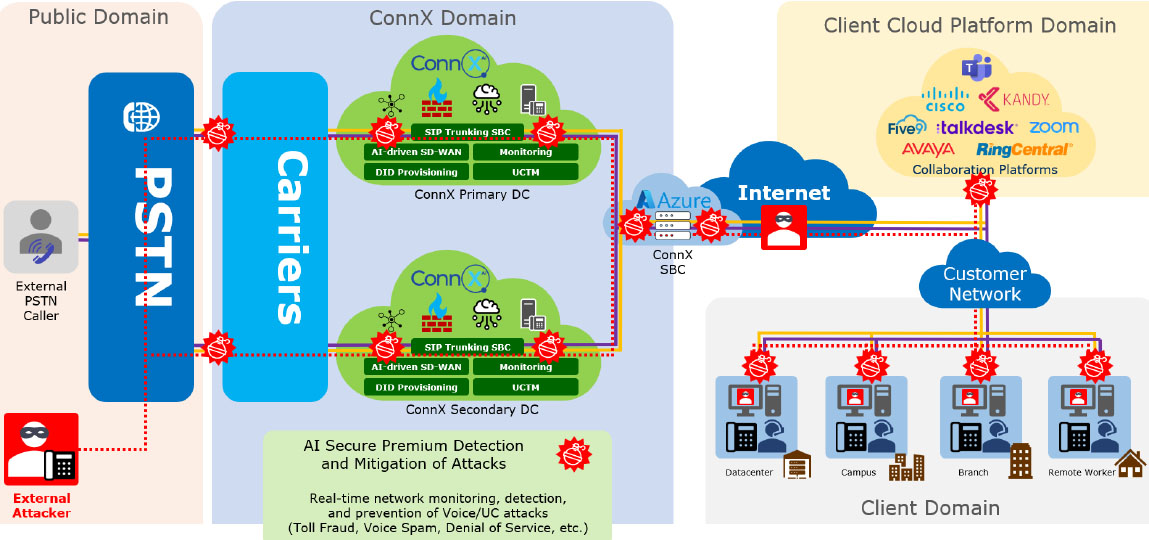
This is what ConnX AI-SECURE calls the Three M approach (Monitor, Measure, and then finally Manage) to collaboration security, which introduces a much more cooperative process for creating and implementing collaboration security policies. The model is a “trust but verify” approach used to monitor and measure behavior, first watch how users are using the WSC platform, and then decide if the usage pattern fits comfortably within the InfoSec framework for the organization.
Certainly, there will always be a minimum level of common-sense policies that get put in place from Day 1 to protect the organization. However, for grey areas which quite often arise with new technologies (such as workstream collaboration), this Three M approach is proving to be effective in applying gentle manipulations to steer and coax employees toward a set of IT decisions and policies, rather than pushing users towards the adoption of unapproved platforms and applications.
Measure: Based on the analytics provided by the software tools, IT can compare the risk exposure profile that it sees with the pre-defined Workstream Collaboration policy. This then allows IT to measure and report on whether any corporate policies are being violated.
Manage: Both IT and end-users can jump into action to either remediate or to create a new policy if governance standards are being exceeded. In many cases, with proactive systems, either pre-defined workflows or AI workflows from software tools will be initiated well before any human touch or intervention is necessary.
CONCLUSION
As IT and security teams battle an influx of unsanctioned tech, the manual work required to effectively manage users while mitigating risk is becoming increasingly complex and time consuming. With the traditional security perimeter growing increasingly porous, threats are no longer purely external — 91% of organizations feel vulnerable to insider threats.
Collaboration security is not just important — it’s paramount. To properly embrace collaboration security, IT and security teams should look to collaboration security tools that make it easier for users to take the right actions while streamlining the organization’s governance of workstream collaboration platforms as a whole.









